This second blog in our series on using OpenTAP for security testing, we take a deep dive into Vulnerability Assessment.
What is a software vulnerability?
A software vulnerability, a.k.a. a security vulnerability or simply a "vulnerability," describes a weakness or flaw in a software system that can be exploited by attackers to compromise the security of the system, its data, or its users. Vulnerabilities can exist in various components of software, including operating systems, drivers, applications, libraries, and firmware.
Software vulnerabilities can arise from a variety of sources, including programming errors, design flaws, configuration mistakes, or unintended interactions between software components.
Common types of software vulnerabilities include:
Buffer Overflows occur when a program writes past the end of a buffer, overwriting and corrupting adjacent memory. Attackers can exploit buffer overflows to inject malicious code or data, crash a program, or gain unauthorized access to resources.
Input Validation vulnerabilities occur when an application fails to validate and sanitize user input. Attackers can exploit input validation flaws to inject malicious code, execute commands, or perform other unauthorized actions.
SQL Injection: vulnerabilities occur in web applications that let users or APIs input SQL queries without validate. Attackers can exploit SQL injection to manipulate database queries, extract sensitive information, or modify database contents.
Cross-Site Scripting (XSS) vulnerabilities occur when a web app outputs untrusted/unvalidated data. Attackers exploit XSS flaws to inject malicious scripts into pages viewed by other users, for unauthorized data disclosure or session hijacking.
Authentication and Authorization vulnerabilities occur when software fails to properly authenticate users or enforce access controls. Attackers can thereby gain unauthorized access to sensitive data or perform actions on behalf of other users.
Denial-of-Service (DoS) Attacks occur when a system is susceptible to attacks that disrupt availability or functionality, usually by consuming excessive system resources, e.g., by overwhelming a TCP/IP stack with packets or connections.
Privilege Escalation occurs when a user or process gains unauthorized access to privileged resources or permissions, most perilously acting as root or superuser.
What is Vulnerability Assessment?
Vulnerability assessment is a systematic process of identifying, quantifying, and prioritizing security vulnerabilities in a system, network, application, or organization. The primary objective of vulnerability assessment is to uncover weaknesses that could be exploited by attackers to compromise the confidentiality, integrity, or availability of the assets being assessed.
Identifying vulnerabilities in source code typically uses a combination of
Humans eyeballing code, often as part of a code review or dedicated research
Tool-based inspection of code for exploitable flaws
Leveraging databases of known vulnerabilities, especially the NIST National Vulnerability Database (NVD). Usually also with tools (SCA)
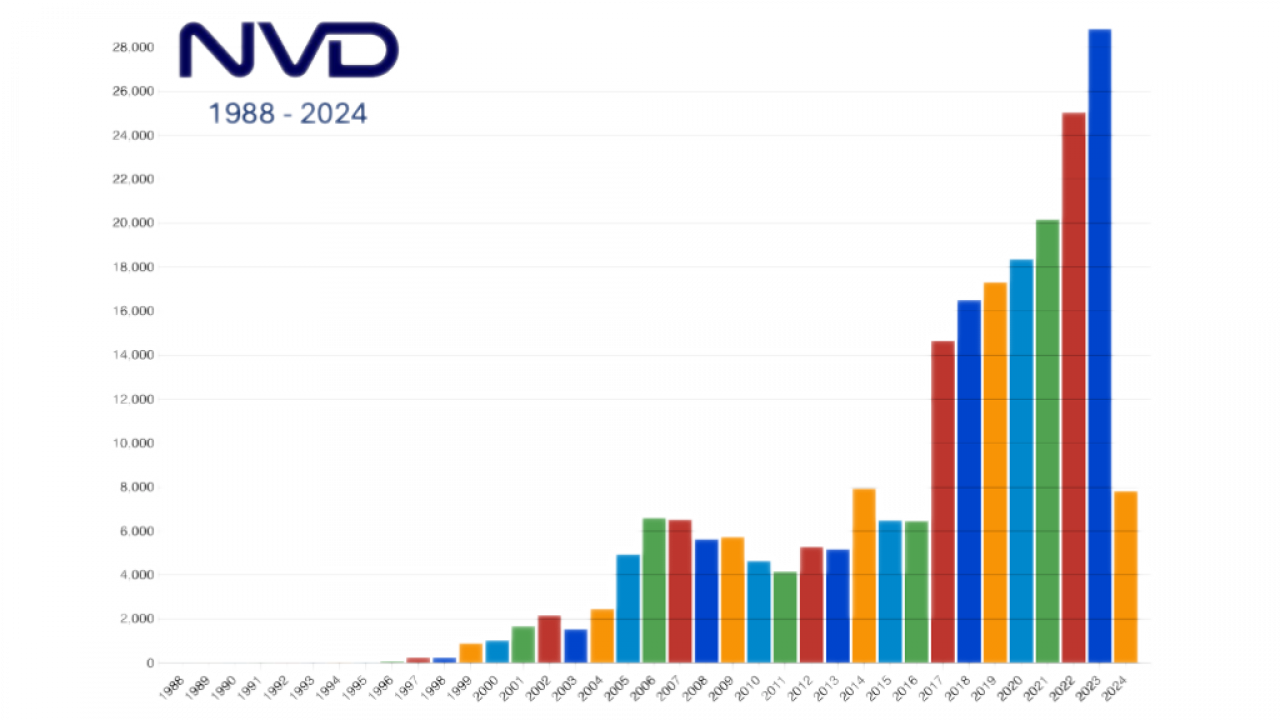
Once a vulnerability has been identified, either in a piece of shared code or a particular application or software stack, the following steps help developers and integrators take appropriate action:
Evaluation and Analysis of vulnerabilities aims to understand potential impact on an organization’s security posture. This process may involve assessing the severity of vulnerabilities, understanding enabled attack vectors, and determining the likelihood of exploitation.
Prioritization – Not all vulnerabilities are equally critical. Prioritizing identified vulnerabilities relies on factors such as severity, potential impact, ease of exploitation, and available resources for mitigation. Prioritization helps organizations focus on addressing the most significant risks first.
Risk Mitigation Strategies can involve implementing security patches, making configuration changes, installing software updates, and deploying new security controls.
Documentation and Reporting involves writing findings of the discovery process, including the identified vulnerabilities, severity ratings, recommended remediation strategies, etc. Reporting the results of the assessment to stakeholders helps in making informed decisions and prioritizing resources for mitigation.
Continuous Monitoring – Vulnerability assessment is not a one-time activity but rather a continuous process. Systems, networks, and applications are constantly evolving, with new vulnerabilities emerging over time. Continuous monitoring and periodic reassessment are essential to maintaining an effective security posture.

The Role of OpenTAP in Vulnerability Assessment
The process of Vulnerability Assessment can be laborious and resource-intensive, especially when performed manually. OpenTAP Test automation can streamline and accelerate vulnerability management in several ways:
Rapid and Continuous Testing: Test automation enables the rapid execution of security tests across application or system components. By automating vulnerability scans, security checks can be conducted continuously and more frequently, resulting in faster identification and remediation.
Scalability: Automation facilitates efficient scaling of vulnerability assessment, permitting testing of large and complex systems without significant manual effort. This scalability also enhances test coverage across environments and configurations.
Consistency and Repeatability: Automated tests provide consistent and repeatable results, reducing the likelihood of human error and ensuring that vulnerability assessments are conducted uniformly across software iterations and versions. Such consistency also helps track changes in security posture over time.
Integration with Development Pipeline: OpenTAP test automation can be integrated into the development pipeline, enabling security testing to occur automatically as part of the continuous integration/continuous deployment (CI/CD) process. This integration constitutes a “shift left”, with security checks occurring early and frequently in the development lifecycle, minimizing risk of introducing vulnerabilities into production environments.
Faster Feedback: Automated vulnerability assessment provides faster feedback to dev teams, letting them address security issues as they arise. Such an agile approach helps in reducing time-to-fix for vulnerabilities and mitigates their impact on the overall security of the system.
Prioritization of Vulnerabilities: Manual prioritization can often be subjective. Automation tools can more consistently prioritize vulnerabilities based on severity, potential impact, and exploitability (based on CVE descriptions and/or internal criteria). Automating prioritization helps organizations to focus resources on addressing the most critical security issues first, more efficiently allocating resources and mitigating the highest risks.
Integration with Security Tools: Automated vulnerability assessment tools can integrate with other security software and platforms, such as vulnerability scanners, static code analysis tools, threat intelligence and event management (SIEM) systems. This integration enhances overall security posture by aggregating and correlating security data from multiple sources.
Customization and Extensibility: Automated vulnerability assessment frameworks often provide flexibility for customization and extension, allowing organizations to tailor security tests to their specific requirements and environments. Such customization ensures that vulnerability assessments align closely with bespoke organization security needs.
Conclusion
Overall, test automation accelerates vulnerability assessment and management by enabling faster detection, remediation, and prevention of security vulnerabilities throughout the software development lifecycle. It helps organizations improve their security posture, reduce risks, and enhance the resilience of their applications against cyber threats.