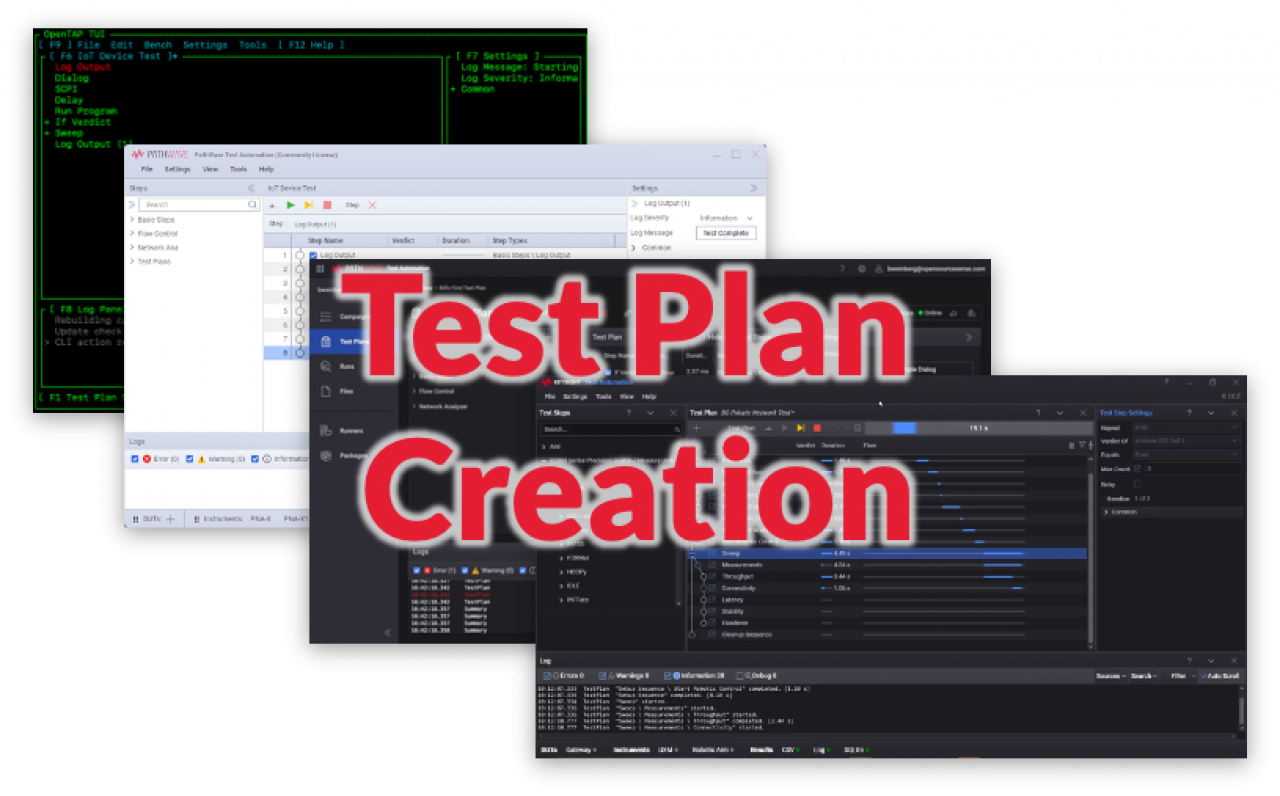
The OpenTAP platform, and Keysight PathWave Test Automation products built with it, consume and interpret Test Plans. Test Plans don't spontaneously spring into existence, and they almost always evolve over time, requiring tools to compose and maintain them.
This blog reviews options for building and modifying OpenTAP test plans, including open source, and community-licensed and commercially-licensed tools from Keysight.